In mid-May, an IT security incident became known that affected a large number of HPC systems worldwide. It took several weeks until the systems could be made available to users again, often only with significant restrictions. The two high-performance computers ForHLR II (Tier-2) and bwUniCluster 2.0 (Tier-3) at KIT were put back into operation in mid-June. During the first out of three phases of the recommissioning process coordinated with the other operators in the federal state of Baden-Wuerttemberg, the use of SSH keys was no longer possible. This caused severe restrictions for the scientific communities, especially on the Tier-2 system, since the HPC systems could no longer be integrated into automated scientific workflows.
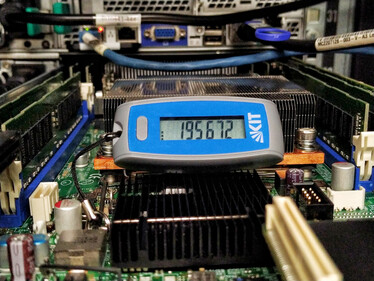
Within just a few weeks, the SCC has now successfully introduced 2-factor authentication (2FA) for all HPC systems using time-based one-time passwords (TOTP). So-called hardware or software tokens can be used to generate the one-time passwords. KIT employees already receive a hardware token for access to critical services such as the SAP portal or campus management. These can now also be used to access the HPC systems. A wide range of software token solutions, including apps for mobile devices, is available to users from other institutions. Registration and management of the tokens is handled by the web portal of the federal identity management system bwIDM.
In combination with the 2FA, the use of SSH keys is now possible again. These keys must also be managed via bwIDM. There are two types of SSH keys: those for interactive use and those for workflow automation (so-called “command keys”). SSH keys registered for interactive use allow the execution of any commands and require additional authentication with a time-based one-time password as a second factor. The second factor has to be entered once per hour at maximum. Command keys can be used without 2FA and thus in an automated fashion. However, they must be restricted to a single command and have to be cleared by the HPC operations team.
Other operators from the bwHPC project are planning to introduce 2-factor authentication based on the new components developed for bwIDM. The source code is available to interested parties under an open source license.
Further information on 2-factor authentication for the HPC systems can be found in the user documentations for ForHLR II and bwUniCluster 2.0.