-
Netzbasierte Sicherheitssysteme
- Schutz vor unberechtigten Zugriffen auf Netzsegmente innerhalb des KIT (Firewall).
- Kontakt:firewall@scc.kit.edu
Es werden Firewalls betrieben, um das netzbasierte Sicherheitskonzept umzusetzen.
Netzbasiertes Sicherheitskonzept
Das netzbasierte Sicherheitskonzept ist ein Teil der Schutzmaßnahmen, die am KIT zum Zugriffschutz auf Netzbasis und zur Abwehr von Computersabotage dienen. Das KIT-Netzwerk ist hierzu mehrstufig in verschiedene Sicherheitsstufen aufgeteilt:
KIT Extranet(A) /KIT Extranet mit Firewall(B) für die Anbindung von Dritten, die in Kooperationen mit dem KIT stehen, ohne IntranetzugriffKIT Intranet mit Stufe-1-Firewall(C) für den Schutz vor unberechtigtem Zugriff aus dem InternetKIT Intranet mit Stufe-2-Firewall(D) /KIT Intranet mit Quarantäne-Firewall(D) für den zusätzlichen Schutz vor Zugriffen aus anderen Netzsegmenten am KITKIT Firewall-Bypass(E) für Systeme, die sowohl aus dem Internet, als auch aus dem Intranet einen breitbandigen oder latenzarmen Zugriff benötigen
In folgender Abbildung ist die Aufteilung des KIT-Netzwerks in die verschiedenen Sicherheitsstufen A bis E schematisch dargestellt und in den folgenden Abschnitten werden die Sicherheitsstufen beschrieben.
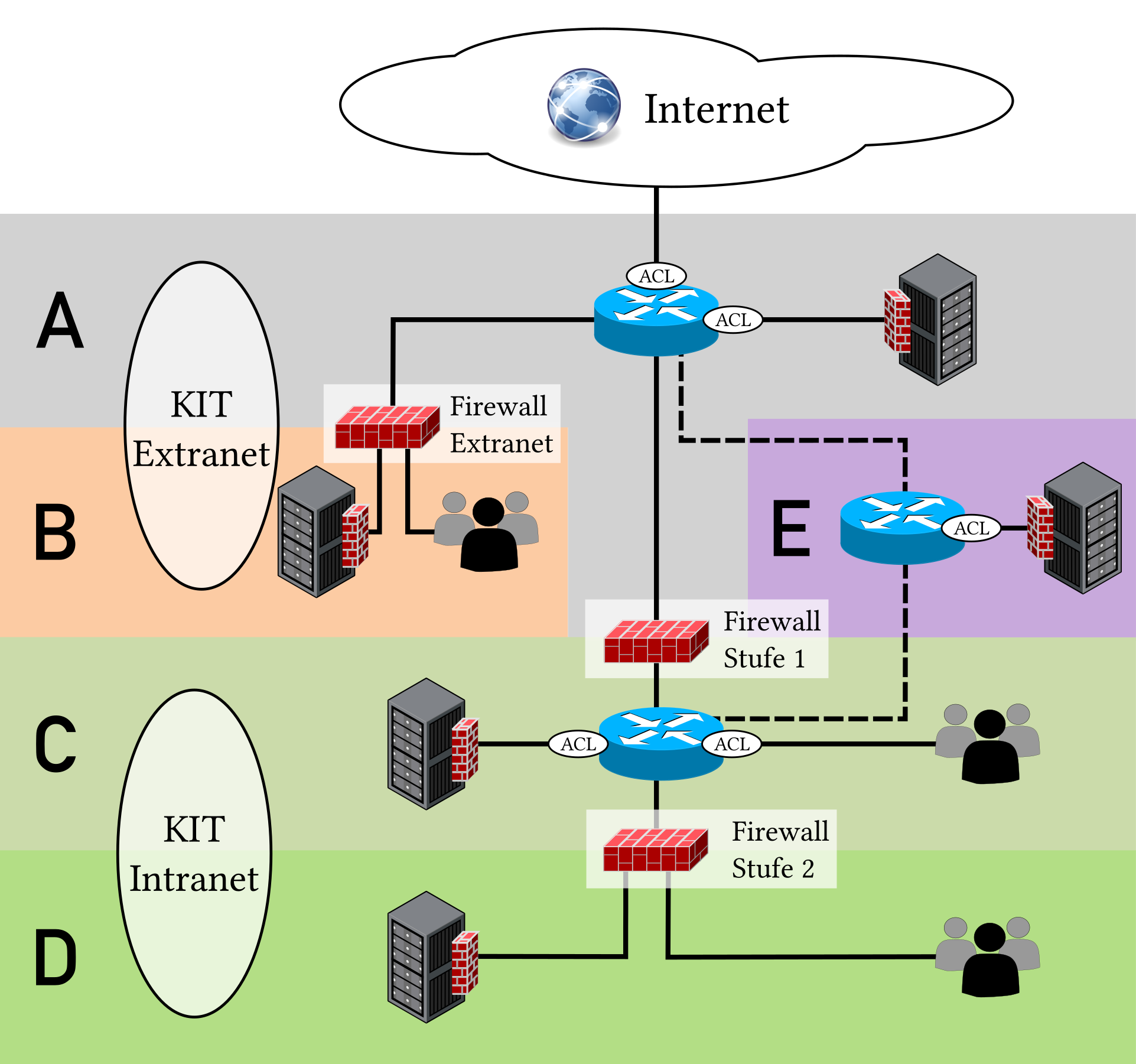
Die Sicherheitsstufen werden durch zentral verwaltete Firewalls für eine einfache netzbasierte Zugriffskontrolle abgesichert. Zu beachten ist, dass die zentral verwalteten Firewalls nur einen rudimentären Schutz gegen Angriffe bieten. Neben dem Schutz durch die zentral verwalteten Firewalls sollte jedes System am KIT möglichst zusätzlich durch eine lokale Software-Firewall (Host Firewall) geschützt sein, immer auf dem aktuellsten Softwarestand betrieben und laufend an die sich ändernde Sicherheitslandschaft angepasst werden.
Schutz vor unberechtigten Endgeräten innerhalb des Netzsegments bietet NAC (Network Access Control). Hier werden unterschiedliche Verfahren angeboten:
- MAC-basierte Authentifizierzung an Dosen / Switchports
- MAC- und Passwort-basierte Authentifizierung im WLAN (KIT-IoT)
- Benutzername/Passwort-basierte Authentifizierung im WLAN und VPN; im VPN ggf. mit 2FA
Grundsätzlich ist zu beachten, dass der Faktor Mensch eine große Rolle zur Abwehr von Computersabotage spielt. Regelmäßige Fortbildungen im Bereicht der Computersicherheit sind daher unabdingbar.
Portsperren an der Außenanbindung
An der Außenanbindung findet die erste Schutzmaßnahme statt. Zustandslose Filter verhindern die eingehende Kommunikation zu bestimmten Ports, die beispielsweise von für Computersabotage anfälligen Diensten genutzt werden. Die gesperrten Protokolle/Ports können der folgenden Tabelle entnommen werden.
| Port / Protokoll | Dienst |
|---|---|
| 25/TCP, 25/UDP | SMTP |
| 53/TCP, 53/UDP | DNS |
| 69/UDP | TFTP |
| 135/TCP, 135/UDP, 593/TCP | Microsoft Windows RPC |
| 137-139/TCP, 137-139/UDP | NetBIOS |
| 161/UDP | SNMP |
| 179/TCP | BGP |
| 445/TCP, 445/UDP | CIFS/SMB |
| 111/TCP, 111/UDP | port mapper |
| 548/TCP | AFP |
| 631/TCP, 631/UDP, 445/UDP | IPP |
| 389/TCP, 636/TCP, 389/UDP, 636/UDP | LDAP(s) |
| 873/TCP | rsync |
| 1080/TCP, 1080/UDP | SOCKS |
| 3260/TCP, 3260/UDP | iSCSI |
| 3389/TCP, 3389/UDP | Windows RDP |
| 5800/TCP, 5900/TCP | VNC |
| 5353/TCP, 5353/UDP | mDNS |
| 11211/UDP | memcached |
Zudem wird eingehend entsprechend der Empfehlung von RFC 4890 ICMPv6 bis auf folgende Typen blockiert:
| Type | Code | Name |
|---|---|---|
| 1 | Destination Unreachable | |
| 2 | Packet Too Big | |
| 3 | 0 | hop limit exceeded in transit |
| 3 | 1 | fragment reassembly time exceeded |
| 4 | 0 | erroneous header field encountered |
| 4 | 1 | unrecognized Next Header type encountered |
| 4 | 2 | unrecognized IPv6 option encountered |
| 128 | Echo Request | |
| 129 | Echo Reply | |
| 144 | Home Agent Address Discovery | |
| 145 | Home Agent Address Discovery | |
| 146 | Mobile Prefix Solicitation | |
| 147 | Mobile Prefix Advertisement |
Zudem wird eingehend entsprechend der Empfehlung von draft-ietf-opsec-icmp-filtering-04 ICMPv4 bis auf folgende Typen blockiert:
| Type | Name |
|---|---|
| 0 | Echo Reply |
| 3 | Destination Unreachable |
| 8 | Echo |
| 11 | Time Exceeded |
Für ausgehenden Datenverkehr wird die Kommunikation mittels folgender Protokolle unterbunden:
| Port / Protokoll | Dienst |
|---|---|
| 25/TCP | SMTP |
Ausnahmen von den oben genannten Sperren sind nur in begründeten Ausnahmenfällen möglich, beispielweise für die vom SCC bereitgestellten DNS-Dienst und E-Mail-Dienste zum Empfangen bzw. Versenden von E-Mails.).
An allen Außenanbindungen sind weiterhin Antispoofing-Regeln nach RFC 2827 / BCP 38 implementiert. Eingehender Datenverkehr mit Absenderadressen aus den Präfixen des KIT werden blockiert.
Sicherheitsstufen
Allgemeines
Unabhängig von der Sicherheitsstufe ist an den Gateways aller Benutzer- und Servernetzsegmente (BCDs) Antispoofing nach RFC 2827 / BCP 38 konfiguriert. Pakete mit Absenderadresse außerhalb des Netzsegments werden verworfen.
Im NATVS+ können einfache Freischaltungen auf den Firewalls durch Netzbetreuer konfiguriert werden, um Dienste aus dem Internet erreichbar zu machen. Dies betrifft Systeme, die in der Sicherheitstufe B, C oder D angebunden sind. Freischaltungen für Ports, die an den Außenanbindungen gesperrt sind (siehe oben), sind unwirksam.
Für komplexere Freischaltungen, wie die Einschränkung auf bestimmte Quell-IP-Adressen, gibt es derzeit noch keine Selbstverwaltungsoberfläche. Diese Freischaltung können vom Netzbetreuer beim Firewall-Team des SCC (firewall∂scc.kit.edu) formlos per E-Mail beantragt werden.
Sicherheitsstufe 1
Ziel der Stufe 1 ist die Abschottung von Systemen gegenüber dem Internet. Als Grundsatz gilt: Auf von innen initiierte Verbindungen darf von außen geantwortet werden. Ein Verbindungsaufbau von außen ist nicht möglich. Dieser Grundsatz gilt gleichermaßen für private und öffentliche IP-Adressen.
Da private Adressen nur innerhalb einer Einrichtung Gültigkeit haben, ist für die Kommunikation dieser Systeme mit dem Internet der Einsatz von Application Gateways oder einer Adressumsetzung erforderlich. Im Bereich der Application Gateways werden seitens des SCC Web-Proxies und Mail-Server angeboten. Für alle anderen Protokolle und Anwendungen findet zur Kommunikation mit dem Internet bei Nutzung einer privaten IP-Adresse eine Adressumsetzung (PAT/NAT, Port/Network Address Translation) in eine öffentliche IP-Adresse statt. Dieser Dienst wird zentralisiert durch die Firewall Stufe 1 realisiert.
Freischaltungen in der Firewall für Zugriffe aus dem Internet auf interne Systeme mit öffentlichen IP-Adressen sind auf zwei Wegen möglich.
Soll ein Dienst mit weltweit allen Quell-IP-Adressen zugänglich sein, erfolgt die Freischaltung über NATVS+, einer Eigenentwicklung des SCC. NATVS+ verfügt über ein User-Interface, das den DNSVS-Betreuern des jeweiligen Adressbereichs eine selbständige Verwaltung ihrer Freischaltungen bietet. Freischaltungen der oben genannten, am Internet-Uplink gesperrten Ports sind unwirksam. Die Übertragung der in NATVS+ gemachten Änderungen auf die Firewalls geschieht automatisiert jede Stunde.
Freischaltungswünsche mit Einschränkung auf bestimmte Quell-IP-Adressen müssen über den zuständigen IT-Beauftragten per E-Mail an das Firewall-Team des SCC (firewall∂scc.kit.edu) gerichtet werden.
Sicherheitsstufe 2
Die Sicherheitsstufe 2 entspricht im Ansatz der Implementierung von Sicherheitsstufe 1 mit dem Unterschied, dass eine Gruppe von Systemen zusätzlich auch vor unerwünschten Zugriffen aus dem KIT-Netz geschützt wird. Die zu schützenden Systemen müssen sich jeweils in einem eigenen VLAN befinden.
Freischaltungen für weltweiten Zugriff aus dem Internet erfolgen wie bei Sicherheitsstufe 1 über NATVS+. Davon abweichende Freischaltungen erfolgen auf Antrag durch das Firewall-Team des SCC. Im NETVS können Netzbetreuer einsehen, welcher Sicherheitsstufe (BCD-Sicherheitsstufe) ein Netzsegment (BCD) zugeordnet ist.
KIT Extranet (A)
Die Sicherheitstufe KIT Extranet stellt die externe Anbindung an Forschungsnetze und das Internet bereit. Zudem werden am KIT Extranet im Rahmen von Kooperationen Anbindungen für Dritte realisiert, die keinen Zugriff auf das Intranet erhalten. Beispielsweise sind hier die bwCloud-Instanz am KIT und GridKa angebunden.
Netzsegmente (BCDs), die in der Sicherheitsstufe Extranet angebunden sind, können über rudimentäre zustandlose Filter abgesichert werden, haben im Allgemeinen jedoch weder einen Schutz gegenüber anderen Systemen innerhalb des Extranet, gegenüber dem Intranet oder dem Internet. Auf interne Dienste im KIT Intranet kann aus dem Extranet grundsätzlich nicht zugegriffen werden. Aus dem Intranet kann hingegen auf Dienste im Extranet, soweit die Kommunikation nicht anderweitig unterbunden wird, zugegriffen werden.
Die Sicherheitsstufe KIT Extranet ist vergleichbar mit der Außenanbindung im BSI IT-Grundschutz NET.1.1.A4.
KIT Extranet mit Firewall (B)
Die Sicherheitsstufe KIT Extranet mit Firewall bietet zusätzlich zu dem rudimentären Grundschutz der Sicherheitsstufe KIT Extranet eine Schutz durch eine Firewall. In dieser Sicherheitsstufe werden im Rahmen von Kooperationen Anbindungen für Dritte realisiert
Eingehende Verbindungen in Netzsegmente dieser Sicherheitsstufe werden grundsätzlich unterbunden, so lange diese nicht explizit freigeschaltet sind. Ausgehende Verbindungen sind grundsätzlich erlaubt, wobei der oben genannte Grundschutz der Sicherheitsstufe KIT Extranet zu beachten ist; weitere Einschränkungen können jedoch umgesetzt werden. Netzsegmente (BCDs), die der Sicherheitsstufe KIT Extranet mit Firewall zugeordnet sind, können untereinander ohne Freischaltung nicht kommunizieren.
Für die Sicherheitsstufe KIT Extranet mit Firewall ist im BSI IT-Grundschutz NET.1.1.A4 nicht direkt einer Zone zuordenbar, ist jedoch am ehesten vergleichbar mit der Außenanbindung.
KIT Intranet mit Stufe-1-Firewall (C)
Die Sicherheitsstufe KIT Intranet mit Stufe-1-Firewall (früher auch Backbone genannt) ist das primäre interne Netzwerk am KIT und bietet zusätzlich zu dem rudimentären Grundschutz der Sicherheitsstufe KIT Extranet eine Schutz durch eine Firewall:
Eingehende Verbindungen aus dem Internet in Netzsegmente dieser Sicherheitsstufe werden grundsätzlich unterbunden, soweit nicht eine im NATVS+ konfigurierte oder beim Firewall-Team angeforderte Freischaltung eingerichtet ist. Verbindungen in das Internet/Extranet sind grundsätzlich erlaubt, so lange diese nicht explizit gesperrt sind.
Systeme, die über Netzsegmente (BCDs) in dieser Sicherheitsstufe angebunden sind, können grundsätzlich untereinander frei kommunizieren. In dieser Sicherheitsstufe werden Server und Clients mit mittlerem Schutzbedarf angebunden. Weiterhin sind in dieser Sicherheitsstufe die allgemeinen VPN- und WLAN-Netze angebunden.
Insbesondere Dienste, die innerhalb des KITs eine hohe Bandbreite benötigen, wie zum Beispiel die Fileserver des SCC, sind in dieser Sicherheitsstufe angebunden.
Damit private IPv4-Adressen auf Ressourcen im Internet zugreifen können, wird auf der Stufe-1-Firewall eine Übersetzung in geteilte öffentliche IPv4-Adressen vorgenommen. (Network Adress Translation (NAT)). Pro Netzsegment kann optional eine dedizierte öffentliche IPv4-Adresse für NAT eingerichtet werden. “Portweiterleitungen” für eingehende Verbindungen sind generell nicht möglich.
Die Sicherheitsstufe KIT Intranet mit Stufe-1-Firewall ist vergleichbar mit der DMZ im BSI IT-Grundschutz NET.1.1.A4.
KIT Intranet mit Stufe 2 Firewall (D)
Die Sicherheitsstufe KIT Intranet mit Stufe-2-Firewall ist mit einer zweiten Firewall gegenüber der Sicherheitsstufe KIT Intranet mit Stufe-1-Firewall (C) geschützt. Auf Systeme in Netzsegmente dieser Sicherheitstufe kann nur nach expliziter Freischaltung über das NATVS+ (Freischaltung für Zugriffe aus dem Internet) oder komplexeren Freischaltungen durch das Firewall-Team zugegriffen werden. Zugriffe in die Sicherheitsstufe KIT Intranet mit Stufe-1-Firewall und zum Internet sind standardmäßig erlaubt, sofern sie nicht explizit durch Firewallregeln unterbunden sind. Netzsegmente (BCDs), die der Sicherheitsstufe KIT Intranet mit Stufe-2-Firewall zugeordnet sind, können untereinander ohne Freischaltung im Allgemeinen nicht kommunizieren.
Server und Clients mit erhöhtem Schutzbedarf werden in dieser Sicherheitsstufe angebunden.
Die Sicherheitsstufe KIT Intranet mit Stufe-2-Firewall ist vergleichbar mit dem internen Netz im BSI-Grundschutz NET.1.1.A4.
KIT Intranet mit Quarantäne-Firewall (D)
Die Sicherheitsstufe KIT Intranet mit Quarantäne-Firewall ist mit einer Firewall von der Sicherheitsstufe KIT Intranet mit Stufe-1-Firewall (C) getrennt. Zugriff aus Netzsegmenten in der Sicherheitsstufe KIT Intranet mit Quarantäne-Firewall heraus werden grundsätzlich unterbunden.
Diese BCD ist primär für Server und Clients, die begründet mit veralteten Betriebssystemen oder Softwarestand betrieben werden müssen, gedacht.
Aus technischen Gründen ist eine Kommunikation zwischen zwei Netzsegmenten innerhalb der Sichertheitsstufe KIT Intranet mit Quarantäne-Firewall nicht möglich.
Die Sicherheitsstufe KIT Intranet mit Quarantäne-Firewall ist vergleichbar mit dem internen Netz im BSI-Grundschutz NET.1.1.A4.
KIT Firewall-Bypass (E)
Die Sicherheitsstufe KIT-Firewall-Bypass ist ein Sonderfall. Es besteht keine Absicherung durch eine zentrale Firewall, weder zum Extranet noch zum Intranet. Diese Sicherheitsstufe ist für Server gedacht, die sowohl aus dem Internet, als auch aus dem Intranet mit hoher Bandbreite oder niedriger Latenz erreicht werden müssen. Hierunter fallen beispielsweise die VPN-Server oder Speichersysteme, die auch anderen Einrichtungen einen Zugriff mit hoher Bandbreite ermöglichen. Systeme, die in dieser Sicherheitsstufe betrieben werden, müssen zwingend über lokale Software-Firewalls gesichert werden. Eine Anbindung in dieser Sicherheitsstufe ist nur in Ausnahmefällen und nach ausführlicher Beratung möglich. Clients werden in dieser Sicherheitsstufe nicht angebunden.

