-
Federated Login Services (FeLS)
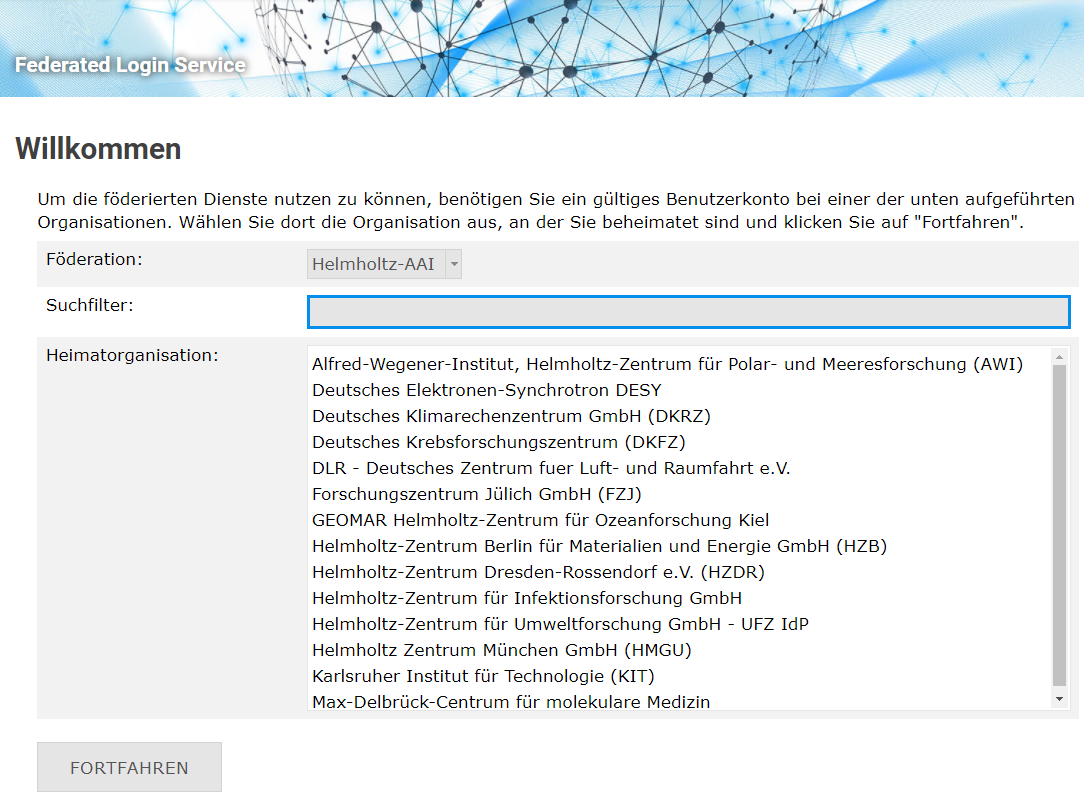
- The Federated Login Services, FeLS for short, provide a secure, central access point (single sign-on) for services that are also used by members of other research institutions. Using the federated open-source identity management system RegApp, registered users from the different institutions are enabled to securely log on to various services. The persons can use the account provided by their home institution.
- Contact:servicedesk@scc.kit.edu
- Advisory services:Michael SimonDr. Matthias Bonn
RegApp - Authentication and Authorization Infrastructure (AAI)
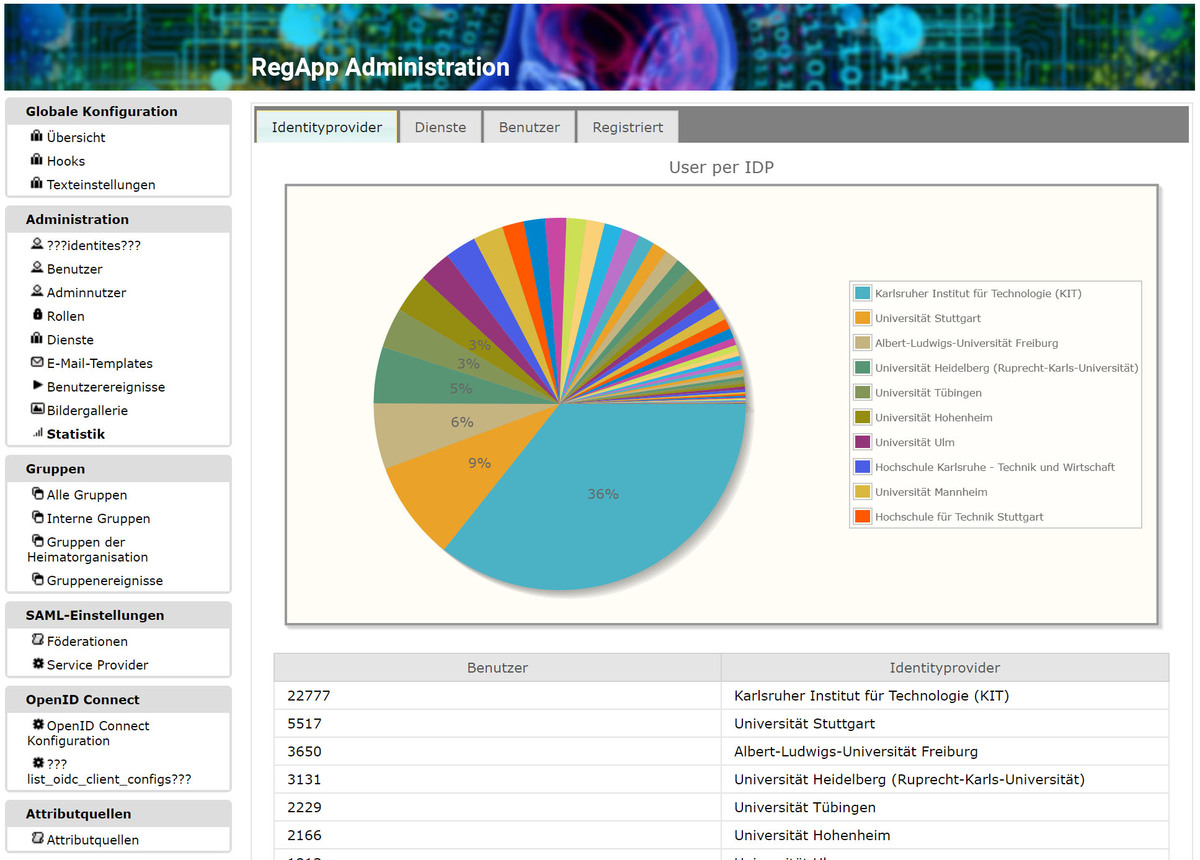
RegApp is a federated open source identity management system, which is mainly developed at the Scientific Computing Center (SCC) at KIT. The currently installed solution enables more than 38,000 registered users from various research institutions, including the Helmholtz Association and universities, to log in to various services, secured by two-factor authorization (2FA). Users can use the account provided by their home institution for this purpose.
Basic Functions as an Identity Proxy for Single Sign-On Environments
- Provisioning and deprovisioning of user identities
- Transparent connection of SAML federations
- SSO protocol proxy OIDC ↔ SAML
- Infrastructure proxy for LDAP services
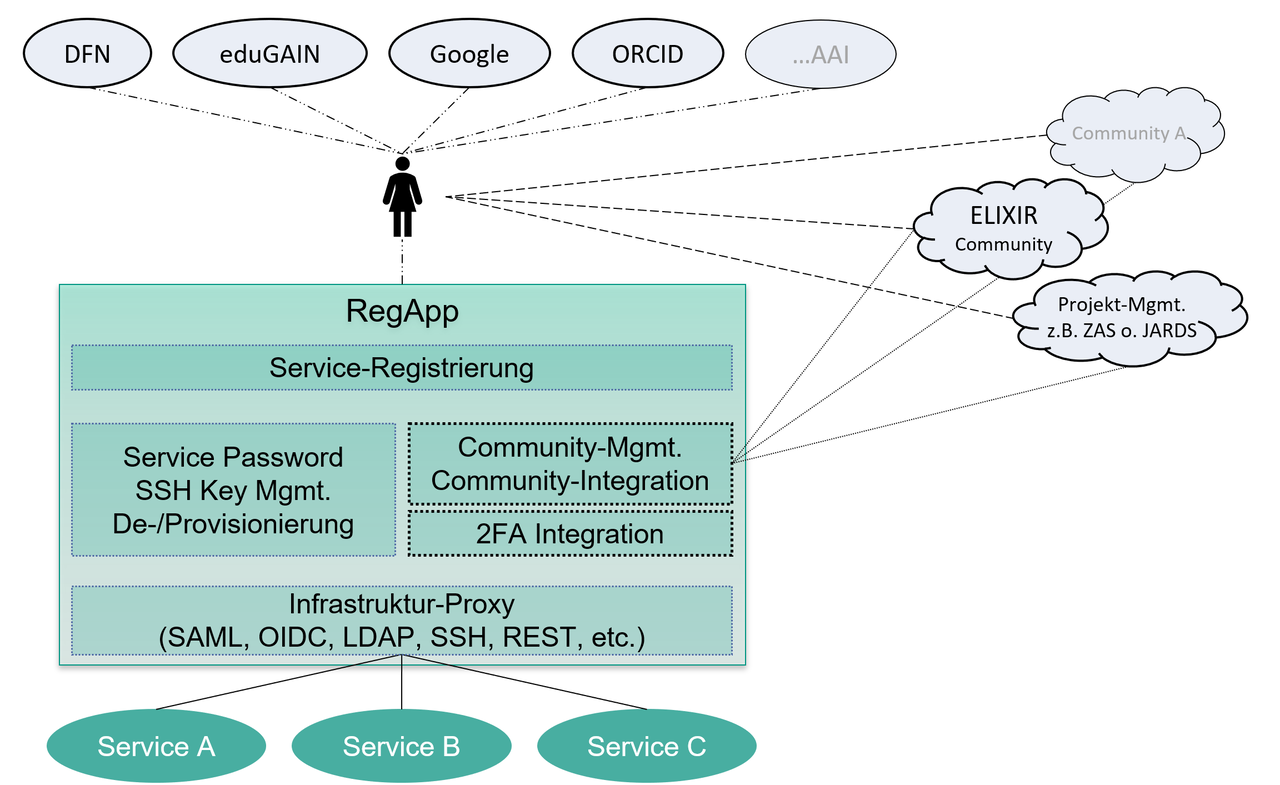
The core functionality of RegApp is to connect services to an authentication and authorization infrastructure (AAI) in a variety of ways. Various integration technologies are available for this purpose: For example, a typical use case would be when a service is not able to directly address SAML-federated identity providers. Here, a so-called IdP-SP proxy can, on the one hand, hide the federated authentication protocol and, on the other hand, hide the complexity of a federation per se by offering the service a suitable SSO access point and by acting as a service provider of the SAML federation, forwarding the users to the home IdPs for authentication. To extend the service connectivity capabilities, RegApp provides both SAML and OpenID connect endpoints. As a protocol translation service, the system maps SAML assertions to OpenID Connect claims. LDAP-based access is also supported to support local accounts with username-password authentication. This addresses all typical SSO scenarios for web-based applications.
Advanced features
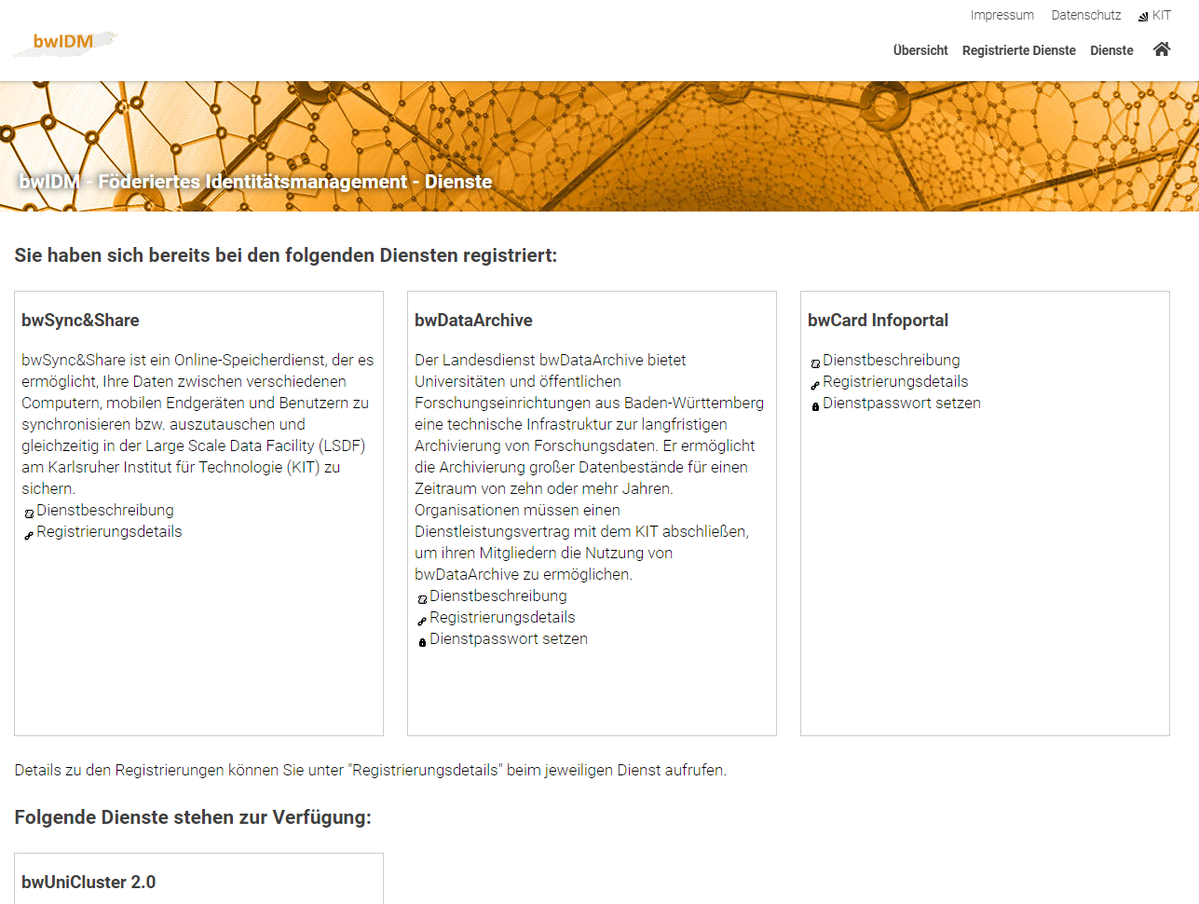
- End-user portal for service registration
- Deposit/management/provisioning of SSH keys
- Multifactor authentication for web and non-web services
Another use case is accessing non-web HPC systems with command line interfaces under advanced security requirements. To support such, the RegApp system provides a portal where authenticated users (e.g., from DFN-AAI-federated organizations) can view a list of all available services and register for them. Depending on the service, a service password must be set and SSH keys with different usage profiles (login vs. remote command execution) can be uploaded. A tethered MFA service (based on LinOTP) is used to validate two-factor TANs and to allow users to register TOTP-based smartphone authenticators through the portal. To enable web-based and command line authentications, some special HTTP REST endpoints are available in addition to SAML, OIDC and LDAP protocols. For web-based logins, the SAML and OIDC endpoints are used. The LDAP endpoint is used for checking service passwords, and the REST endpoints are used for checking the second factor code and downloading the user's SSH keys.
With these building blocks, almost any service can be connected to the DFN-AAI user federation in a secure manner, including step-up authentication with a second factor, even if the user's home IdP does not support it.
Outlook
- Authorization functions based on project groups
- Integration of external research communities
Future developments plan the realization of an administration for project groups and their composition. A project group is to be regarded as a virtual network of user identities and accounts, also known as research community. The focus is on the implementation of the associated processes, such as the (de)provisioning of project groups, and the design and implementation of a meaningful rights/roles concept for managing the groups or their members. Since membership in a project group is the basis for authorization decisions, these memberships should be passed on to the corresponding service or community. Since not every connected service is able to perform user authorization, especially with regard to communities, user authorization will ultimately be available on the proxy side based on account properties or group memberships.
Summary
Following the AARC Blueprint Architecture, the RegApp will be further developed to facilitate the connection of research communities. Following this approach, the implementation of token translation services will enable advanced service integration through modern authentication methods and protocols such as OpenID Connect, an increasingly established standard. This ensures the openness of the system and the future-proof integration of additional data services. Establishing appropriate account linking procedures within RegApp enables the assignment of unique identities in a consistent and uniform manner to HPC clusters and any other connected service, regardless of the access used. Finally, RegApp sets the stage for cross-institutional integration of services and establishes group/role management for cross-regional and national communities with delegation mechanisms. The software is already being used and further developed in the Helmholtz project HIFIS and in the current bwIDM project of the state of Baden-Württemberg.
Source code and availability
The source code of RegApp is available via Git. It is possible to launch a demo instance as a Docker container. The documentation is linked at the respective Git projects.
Gitlab: https://gitlab.kit.edu/kit/reg-app/regapp
Docker: https://gitlab.kit.edu/kit/reg-app/regapp-docker
Mailing list: regapp-users∂lists.kit.edu
References

Detailed information
In the context of bwIDM: https://login.bwidm.de
In the context of Helmholtz-AAI: https://fels.scc.kit.edu
In the context of NFDI: https://regapp.nfdi-aai.de
In the context of NHR: https://www.nhr.kit.edu/english/297.php