Table of contents
sprungmarken_marker_18271
Firewall concepts
The network-based security concept is part of the protective measures at KIT for access protection on a network basis and to defend against computer sabotage. The KIT network is divided into different security levels:
KIT Extranet(A) /KIT Extranet with Firewall(B) for connecting third parties in cooperation with KIT, without intranet accessKIT Intranet with Level 1 Firewall(C) for protection against unauthorized access from the internetKIT Intranet with Level 2 Firewall(D) /KIT Intranet with Quarantine Firewall(D) for additional protection against access from other network segments at KITKIT Firewall Bypass(E) for systems that require broadband or low-latency access from both the internet and the intranet
In the following figure, the division of the KIT network into the various security levels A through E is schematically represented, and the subsequent sections describe these security levels.
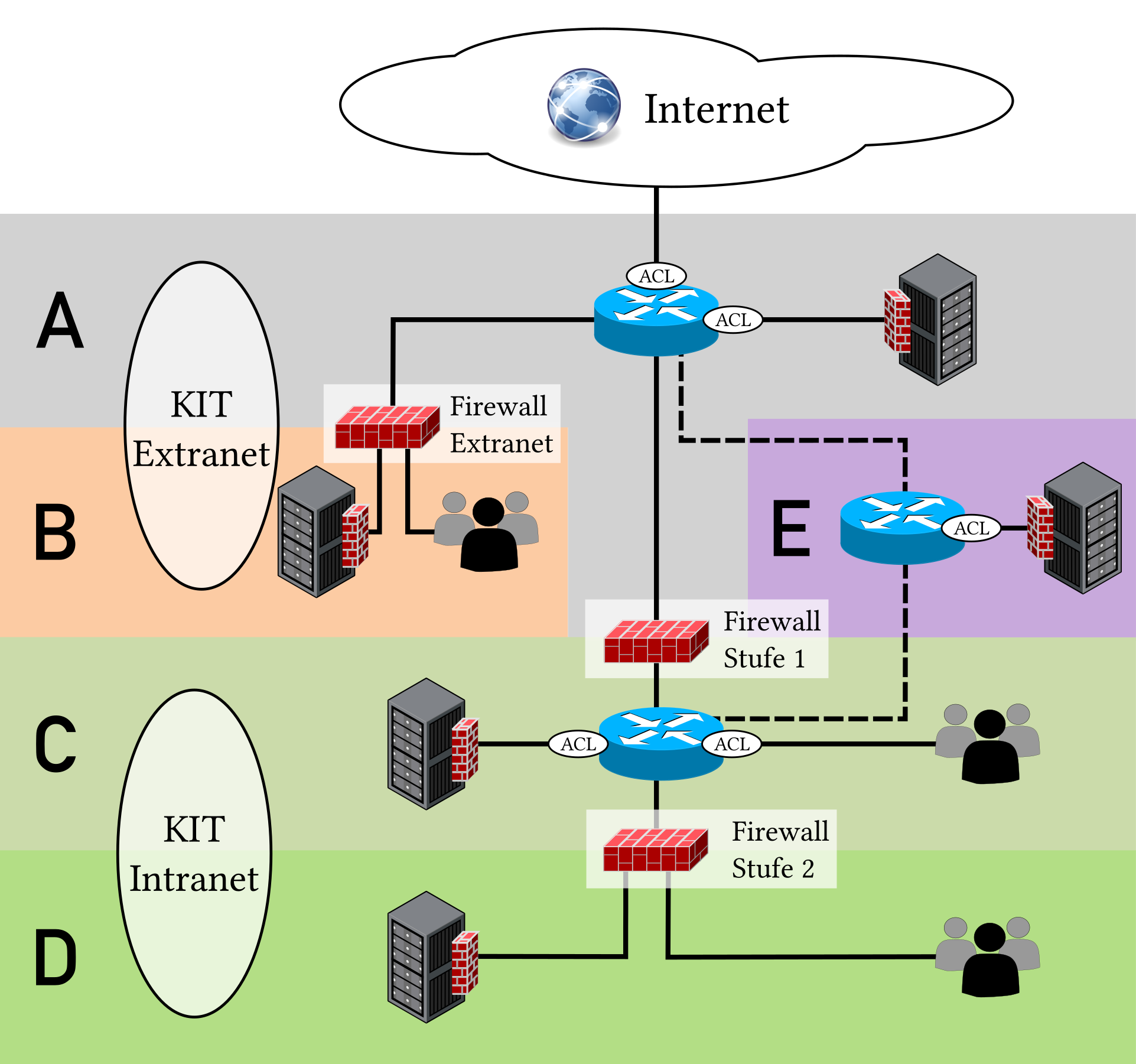
The security levels are secured by centrally managed firewalls for simple network-based access control. It is important to note that centrally managed firewalls provide only rudimentary protection against attacks. In addition to the protection offered by the centrally managed firewalls, every system at KIT should ideally be further protected by a local software firewall (host firewall), always operated on the latest software version, and continuously adapted to the changing security landscape.
Protection against unauthorized devices within the network segment is provided by NAC (Network Access Control). Various methods are offered for this purpose:
- MAC-based authentication at outlets/switch ports
- MAC and password-based authentication in WLAN (KIT-IoT)
- Username/password-based authentication in WLAN and VPN; in VPN with possible 2FA
It is essential to recognize that the human factor plays a significant role in defending against computer sabotage. Therefore, regular training in the field of computer security is indispensable.
Port Blocking at the External Connection
The first line of defense occurs at the external connection. Stateless filters prevent incoming communication to specific ports that are, for instance, used by services susceptible to computer sabotage. The blocked protocols/ports can be found in the table below.
| Port / Protocol | Service |
|---|---|
| 25/TCP, 25/UDP | SMTP |
| 53/TCP, 53/UDP | DNS |
| 69/UDP | TFTP |
| 135/TCP, 135/UDP, 593/TCP | Microsoft Windows RPC |
| 137-139/TCP, 137-139/UDP | NetBIOS |
| 161/UDP | SNMP |
| 179/TCP | BGP |
| 445/TCP, 445/UDP | CIFS/SMB |
| 111/TCP, 111/UDP | port mapper |
| 548/TCP | AFP |
| 631/TCP, 631/UDP, 445/UDP | IPP |
| 389/TCP, 636/TCP, 389/UDP, 636/UDP | LDAP(s) |
| 873/TCP | rsync |
| 1080/TCP, 1080/UDP | SOCKS |
| 3260/TCP, 3260/UDP | iSCSI |
| 3389/TCP, 3389/UDP | Windows RDP |
| 5800/TCP, 5900/TCP | VNC |
| 5353/TCP, 5353/UDP | mDNS |
| 11211/UDP | memcached |
Additionally, incoming ICMPv6 traffic is blocked in accordance with the recommendation from RFC 4890, except for the following types:
| Type | Code | Name |
|---|---|---|
| 1 | Destination Unreachable | |
| 2 | Packet Too Big | |
| 3 | 0 | hop limit exceeded in transit |
| 3 | 1 | fragment reassembly time exceeded |
| 4 | 0 | erroneous header field encountered |
| 4 | 1 | unrecognized Next Header type encountered |
| 4 | 2 | unrecognized IPv6 option encountered |
| 128 | Echo Request | |
| 129 | Echo Reply | |
| 144 | Home Agent Address Discovery | |
| 145 | Home Agent Address Discovery | |
| 146 | Mobile Prefix Solicitation | |
| 147 | Mobile Prefix Advertisement |
Additionally, incoming ICMPv4 traffic is blocked in accordance with the recommendation from draft-ietf-opsec-icmp-filtering-04, except for the following types:
| Type | Name |
|---|---|
| 0 | Echo Reply |
| 3 | Destination Unreachable |
| 8 | Echo |
| 11 | Time Exceeded |
For outgoing traffic, communication is prevented using the following protocols:
| Port / Protocol | Service |
|---|---|
| 25/TCP | SMTP |
Exceptions to the aforementioned blocks are only possible in justified exceptional cases, such as for the DNS services and email services for receiving and sending emails provided by the SCC.
Anti-spoofing rules according to RFC 2827 / BCP 38 are implemented at all external connections. Incoming traffic with source addresses from the prefixes of KIT is blocked.
Security Levels
General Information
Regardless of the security level, anti-spoofing according to RFC 2827 / BCP 38 is configured at the gateways of all user and server network segments (BCDs). Packets with a source address outside of the network segment are discarded.
In NATVS+, simple activations on the firewalls can be configured by network operators to make services accessible from the internet. This applies to systems that are connected at security levels B, C, or D. Activations for ports that are blocked at the external connections (see above) are ineffective.
For more complex activations, such as restrictions to specific source IP addresses, there is currently no self-service interface available. These activations can be requested informally by the network operator from the SCC firewall team via email (firewall∂scc.kit.edu).
Security Level 1
The goal of Level 1 is to isolate systems from the internet. The principle is that responses can be made to connections initiated from within, but initiating a connection from the outside is not possible. This principle applies to both private and public IP addresses.
Since private addresses are only valid within an organization, communication of these systems with the internet requires the use of application gateways or an address translation. The SCC offers web proxies and mail servers in the area of application gateways. For all other protocols and applications, communication with the internet using a private IP address involves an address translation (PAT/NAT, Port/Network Address Translation) into a public IP address. This service is centralized through the Level 1 Firewall.
Activations in the firewall for internet access to internal systems with public IP addresses are possible in two ways.
If a service should be accessible with all source IP addresses worldwide, the activation is done via NATVS+, a self service portal developed by the SCC. NATVS+ has a user interface that allows the DNSVS operators of the respective address range to independently manage their activations. Activations for ports blocked at the internet uplink are ineffective. The changes made in NATVS+ are automatically transferred to the firewalls every hour.
Requests for activation with restrictions to certain source IP addresses must be directed to the SCC firewall team (firewall∂scc.kit.edu) via email by the responsible IT officer.
Security Level 2
Level 2 follows the approach of implementing Security Level 1, with the difference that a group of systems is additionally protected against unwanted access from within the KIT network. The systems to be protected must each be in their own VLAN.
Activations for global access from the internet are handled as in Security Level 1 via NATVS+. Activations that deviate from this are made upon request through the SCC Firewall Team. In NETVS network operators can view which security level (BCD security level) a network segment (BCD) is assigned to.
KIT Extranet (A)
The KIT Extranet security level provides external connectivity to research networks and the internet. Additionally, within the framework of collaborations, connections for third parties are established at the KIT Extranet, who do not receive access to the intranet. Examples include the bwCloud instance at KIT and GridKa.
Network segments (BCDs) connected at the Extranet security level may be secured with basic stateless filters but generally do not have protection against other systems within the Extranet, against the Intranet, or the internet. Access to internal services in the KIT Intranet from the Extranet is fundamentally not possible. However, services in the Extranet can be accessed from the Intranet, provided that the communication is not otherwise restricted.
The KIT Extranet security level is comparable to the external connection in the BSI IT-Grundschutz NET.1.1.A4.
KIT Extranet with Firewall (B)
The KIT Extranet with Firewall security level provides additional protection through a firewall, beyond the rudimentary basic protection of the KIT Extranet security level. In this security level, connections for third parties are established within the scope of collaborations.
Incoming connections to network segments of this security level are generally blocked unless explicitly activated. Outgoing connections are fundamentally allowed, but the aforementioned basic protection of the KIT Extranet security level should be observed; however, further restrictions can be implemented. Network segments (BCDs) assigned to the KIT Extranet with Firewall security level cannot communicate with each other without activation.
The KIT Extranet with Firewall security level cannot be directly associated with a zone in the BSI IT-Grundschutz NET.1.1.A4, but it is most comparable to the external connection.
KIT Intranet with Level 1 Firewall (C)
The KIT Intranet with Level 1 Firewall (formerly also called Backbone) is the primary internal network at KIT and, in addition to the rudimentary basic protection of the KIT Extranet security level, provides protection through a firewall:
Incoming connections from the internet to network segments of this security level are generally blocked unless an activation has been configured in NATVS+ or requested from the firewall team. Connections to the internet/Extranet are fundamentally allowed as long as they are not explicitly blocked.
Systems connected through network segments (BCDs) at this security level can generally communicate freely with each other. This security level connects servers and clients with medium protection needs. Additionally, general VPN and WLAN networks are connected at this security level.
Services within KIT that require high bandwidth, such as SCC's file servers, are connected at this security level.
To enable private IPv4 addresses to access resources on the internet, a translation to shared public IPv4 addresses is performed on the Level 1 Firewall (Network Address Translation (NAT)). Optionally, a dedicated public IPv4 address for NAT can be set up for each network segment. "Port forwarding" for incoming connections is generally not possible.
The KIT Intranet with Level 1 Firewall security level is comparable to the DMZ in the BSI IT-Grundschutz NET.1.1.A4.
KIT Intranet with Level 2 Firewall (D)
The security level KIT Intranet with Level 2 Firewall is protected by a second firewall compared to the KIT Intranet with Level 1 Firewall (C) security level. Access to systems within this security level's network segments is possible only after explicit activation through NATVS+ (activation for internet access) or more complex activations by the firewall team. Accesses to the KIT Intranet with Level 1 Firewall security level and to the internet are allowed by default, as long as they are not explicitly blocked by firewall rules. Network segments (BCDs) assigned to the KIT Intranet with Level 2 Firewall security level generally cannot communicate with each other without activation.
Servers and clients with increased protection needs are connected at this security level.
The KIT Intranet with Level 2 Firewall security level is comparable to the internal network in the BSI IT-Grundschutz NET.1.1.A4.
KIT Intranet with Quarantine Firewall (D)
The KIT Intranet with Quarantine Firewall security level is separated by a firewall from the KIT Intranet with Level 1 Firewall (C) security level. Access from network segments within the KIT Intranet with Quarantine Firewall security level is fundamentally blocked.
This BCD is primarily intended for servers and clients that must be operated with outdated operating systems or software versions for justified reasons.
Due to technical reasons, communication between two network segments within the KIT Intranet with Quarantine Firewall security level is not possible.
The KIT Intranet with Quarantine Firewall security level is comparable to the internal network in the BSI IT-Grundschutz NET.1.1.A4.
KIT Firewall Bypass (E)
The KIT Firewall Bypass security level is a special case. There is no protection through a central firewall, neither to the Extranet nor to the Intranet. This security level is intended for servers that need to be accessed with high bandwidth or low latency from both the internet and the intranet. Examples include VPN servers or storage systems that also provide high-bandwidth access to other institutions. Systems operating at this security level must be secured with local software firewalls mandatorily. Connection at this security level is only possible in exceptional cases and after thorough consultation. Clients are not connected at this security level.

